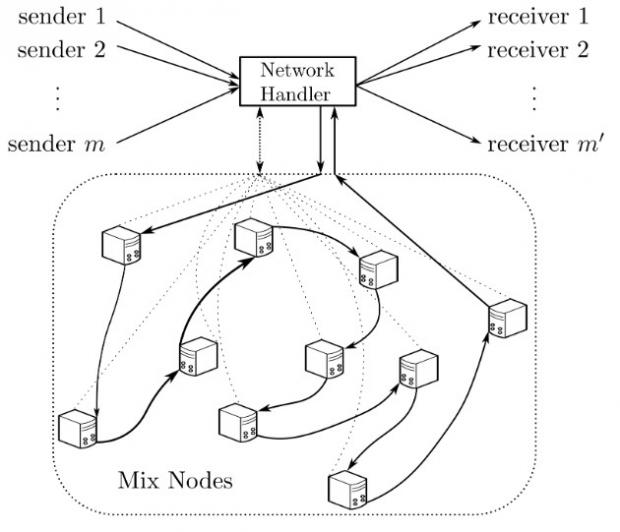
His paper, called “cMix: Anonymization by High-Performance Scalable Mixing,” presents an evolution of the Mix Network concept, called cMix. The paper addresses several issues that governments and regular users had with the Mix Network. According to Chaum, now researchers plan to use this new cryptography protocol to build their own, more secure PrivaTegrity network, as an alternative to Tor. According to their research paper (page 1 – Section I, and page 4 – Chapter III-D), for each communications path established in a cMix network, the message sender creates connections with a series of trusted servers, with which it shares a series of keys. When the sender sends out a message, its data is multiplied with all the keys. As the message passes through each server, it is divided with each server’s corresponding key, but also multiplied again by a random number. Messages are then stored randomized in each server’s buffer. When the data needs to be retrieved and sent to the receiver, each server will retrieve the message from its random position, divide out the random numbers, and then multiply it with the recipient’s keys. When the data arrives on the recipient’s computer, their keys are used to divide the data and decrypt the message. Tagging attacks rely on compromising Tor nodes, which on their own allow attackers to tag input slots with their output location. By using cMix’s setup, the protocol is not vulnerable to these type of attacks, unless the malicious actor compromises all the elements of the protocol, which is very rare. Additionally, researchers said that, in PrivaTegrity, tagging attacks are also blocked by how users set up keys with network nodes. “PrivaTegrity aims to provide privacy at a technical level that is not penetrable by nation states,” the researchers claim. “PrivaTegrity implements a new approach to user identification requiring each user to provide a small but different type of identifying information to each mix node.”