Microsoft Word becomes preferred channel for delivering Dridex banking trojanAn EvolutionThe AttackThe Remedy
An Evolution
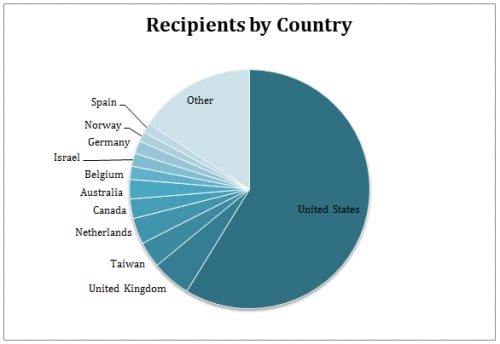
Dridex is the next step in the evolution of the trojan, the predecessor versions being Feodo/Bugat/Cridex Trojans that then developed into Geodo. It preserves the bank information stealing capabilities of its previous versions but changed the method used for compromising the compute. Another change has been the targets. While its predecessor targeted customers of banks in Germany, Dridex banking trojan seems to be specifically targeting American citizens. Like its precursors, Dridex is a sophisticated Banking Trojan, similar to the infamous Zeus malware. Its core functionality is to steal credentials of online banking websites and to allow the cyber criminals to siphon money from victims bank account. Dridex uses an XML-based configuration file to specify which websites it should target and other options for the malware. For instance, the configuration specifies which websites to capture form submissions from, and which to ignore with the following XML. The first wave of Dridex banking trojan began on October 21, with e-mails claiming to carry invoices from Humber Merchant’s group. The country wise breakup of victims are receiving the files containing the Dridex banking trojan as below :
The Attack
The attack is based on the premise of sending the target the infected word file. When the user opens the file, the macro in the file will automatically downloads the trojan from a remote server which the cyber criminals control. Different versions of Dridex will thus be downloaded all having the same purpose, stealing banking credentials. The word documents delivering the Dridex banking trojan contain a complex VBA macro that downloads an executable from one of the following URLs and executes it on the system. These are all legitimate websites that appear to be compromised by the cyber criminals or masterminds running this Dridex campaign. The files are each different versions of the Dridex malware that communicate with their command and control servers over HTTP.
The Remedy
This trojan uses macros in the Office suite. So the best approach to prevent such a trojan is to disable macros right from the beginning. Microsoft realises the flaws in macro use and disables them by default in the Office suite, however there is no patch for such kind of trojan as of yet. A user can however, enable and use them whenever desired. Abuse.ch operates the Feodo Tracker, a service dedicated to keeping an eye on the command and control (C&C) servers used by the actors behind the malware campaign. Out of 93 tracked machines for communications containing the Dridex banking trojan, the service shows that at the moment there are 12 servers online, four of them being located in Russia. Resource : Palo Alto Networks Research Centre